8 C 9 6 2c 12 4c
Greels
Apr 23, 2025 · 5 min read
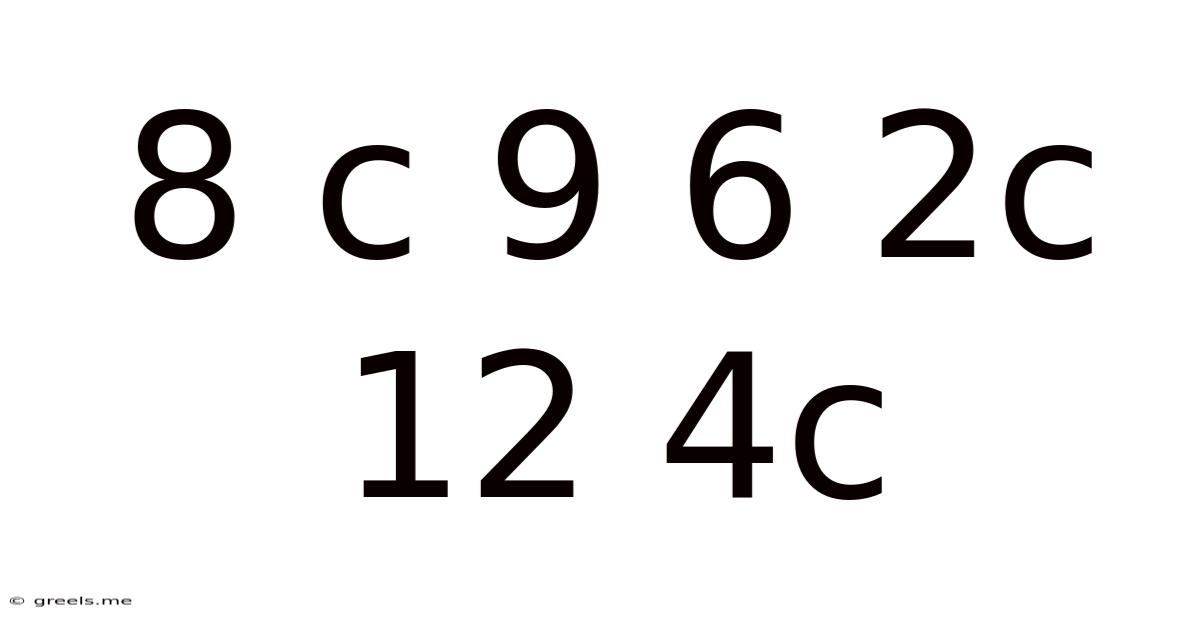
Table of Contents
Decoding the Enigma: 8C 9 6 2C 12 4C and the Art of Cryptography
The seemingly random sequence "8C 9 6 2C 12 4C" might appear meaningless at first glance. However, within this cryptic string lies a fascinating journey into the world of cryptography, a field dedicated to secure communication in the face of potential adversaries. Understanding this sequence requires exploring various cryptographic techniques and their applications in securing sensitive information. This article will delve deep into the potential meanings behind this sequence, exploring different cipher types, their historical significance, and the modern relevance of cryptography in our increasingly digital world.
Potential Interpretations and Cipher Types
The sequence "8C 9 6 2C 12 4C" could represent a variety of encoded messages, depending on the chosen cipher. Let's explore some possibilities:
1. Hexadecimal Representation and its Implications
One possible interpretation is that "8C 9 6 2C 12 4C" is a hexadecimal representation of data. Hexadecimal is a base-16 number system, frequently used in computing to represent binary data in a more human-readable format. Each character in the sequence could correspond to a byte (8 bits) of data. This opens the possibility of several interpretations:
-
ASCII or other character encodings: If we convert each hexadecimal pair into its decimal equivalent and then look up the corresponding ASCII character, we might reveal an encoded message. However, without a key or further context, this approach is purely speculative and likely to yield gibberish.
-
Binary Data: The hexadecimal representation could be directly related to binary data, such as image files, program code, or other forms of computer data. Analyzing the sequence as binary data might reveal patterns or structures. However, this would require specialized tools and a deep understanding of the type of data being encoded.
2. Variations of Substitution Ciphers
Substitution ciphers are fundamental cryptographic techniques where each letter or symbol in the plaintext is replaced with a different letter or symbol according to a specific rule. "8C 9 6 2C 12 4C" could potentially represent a substituted message, but the specific cipher must be known to decipher it.
-
Caesar Cipher: A simple substitution cipher where each letter is shifted a certain number of positions down the alphabet. While unlikely given the mix of numbers and letters, a more complex variant might be applicable.
-
Polyalphabetic Substitution Cipher: These ciphers use multiple substitution alphabets, making them significantly harder to crack than simple substitution ciphers like the Caesar cipher. The Vigenère cipher is a prime example. Analyzing for patterns and frequencies of letters and numbers could help determine the underlying alphabet used.
-
Keyword Ciphers: These ciphers use a keyword to generate a substitution alphabet. The keyword plays a crucial role in deciphering the message, and without knowing the keyword, deciphering becomes far more complex.
3. Exploring More Advanced Techniques
The sequence could also represent a segment of a more complex cryptographic system:
-
Transposition Ciphers: These ciphers rearrange the letters of a message without changing them. Techniques like columnar transposition or rail-fence ciphers might be employed. To decode, we'd need to know the transposition method.
-
Block Ciphers: These ciphers operate on fixed-size blocks of data, encrypting each block individually. Modern block ciphers like AES (Advanced Encryption Standard) are widely used to secure sensitive data. The sequence might be a part of a larger block encrypted using a block cipher. However, without the key, deciphering is computationally infeasible.
-
Stream Ciphers: Stream ciphers encrypt data bit by bit or byte by byte using a keystream. This type of cipher requires a keystream generator and, again, the specific key to decipher.
The Importance of Context and Keys
The crucial element missing from interpreting "8C 9 6 2C 12 4C" is context. Knowing the source of this sequence, the intended recipient, and the circumstances under which it was generated are crucial to determining the type of cipher used and the meaning of the message. Furthermore, keys are essential for deciphering most cryptographic techniques. The key is a secret piece of information that determines the specific transformation applied to the plaintext.
Cryptography: A Historical and Modern Perspective
Cryptography has a rich history, dating back to ancient civilizations. From the Caesar cipher used by Julius Caesar to protect military communications to the more sophisticated techniques used today, the development of cryptography reflects humanity's ongoing struggle to protect sensitive information.
Early Cryptography
Early methods were relatively simple, relying on substitution and transposition techniques. However, as analytical techniques improved, the need for more robust methods became apparent.
Modern Cryptography
The advent of computers revolutionized cryptography. Modern cryptographic techniques rely on complex mathematical algorithms that are computationally difficult to break without the correct key. Public-key cryptography, which uses a pair of keys—a public key for encryption and a private key for decryption—has significantly impacted secure communication over open networks. Examples include RSA and ECC (Elliptic Curve Cryptography).
The Significance of Cryptography in the Digital Age
In our increasingly interconnected world, cryptography is essential for securing digital communication and data. It plays a crucial role in:
-
Data security: Protecting sensitive data such as financial information, personal records, and intellectual property.
-
Network security: Securing computer networks from unauthorized access and cyberattacks.
-
Authentication: Verifying the identity of users and devices.
-
Digital signatures: Ensuring the authenticity and integrity of digital documents.
-
E-commerce: Securing online transactions and protecting customer data.
Conclusion
While we cannot definitively decipher "8C 9 6 2C 12 4C" without more information, exploring its potential interpretations provides a valuable glimpse into the world of cryptography. The sequence could represent data encoded using various techniques, ranging from simple substitution ciphers to sophisticated block or stream ciphers. The importance of context and keys in deciphering encrypted messages cannot be overstated. As technology continues to evolve, the role of cryptography in safeguarding sensitive information will only become more critical. The ongoing quest to develop stronger and more secure cryptographic methods underscores the importance of this fascinating and ever-evolving field. Understanding the fundamentals of cryptography is essential for navigating the complexities of our increasingly digital world and protecting ourselves from the ever-present threat of cyberattacks.
Latest Posts
Related Post
Thank you for visiting our website which covers about 8 C 9 6 2c 12 4c . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.